Risk Register Template Excel Free Download
What Is A Risk Register In Project Management?
Risk Register is a document which stores all the information related the project risks. It includes a wide variety of information for every risk including a limited description, owner, impact etc. The task of managing risks starts when the project is started. To start with, the project manager will conduct a risk assessment workshop to understand the major risks for the project.
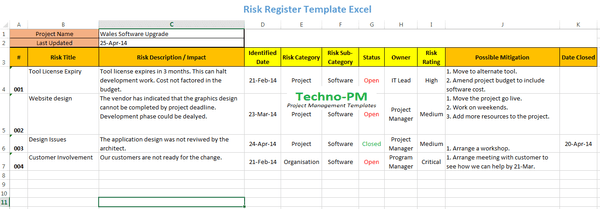
Maintaining a risk register is a very basic task for any project manager. It is often presented as a table, with each risk being awarded a score based on its potential impact and probability.
A risk register is also used as a tracking method of all the projects’ risks, from assessment through managing the risks until they are down to acceptable levels. The tool is managed by the PM or the PMO (or Risk Management Officer {RMO} in large-scale projects).
The register should be made visible to all involved in the project (stakeholders, team members, vendors, clients, etc.) so the awareness of the risk will be high. This assists in mitigating the materialization of each risk.
See our 3 step project risk management process to understand how you can use the risk register to manage project risks.
Why Do We Need A Risk Register?
- The register is an important tracking and monitoring tool of the project and allows visibility of the risks to all those who are involved in it.
- The register tracks the risk from its inception to its materialization or mitigation and shows what the mitigation steps were and how they affected the risk.
- This can be used post factum in order to create lessons learned log or to update best practices and processes/procedures.
- This is an important part of the whole risks management of the project.
- Another important factor which the register answers are documentation of the risks, which is important for the regulatory obligations of the country/field of expertise.
- The register should be tracked on a weekly / bi-weekly basis, depending on the projects’ duration, innovation level, and complexity.
- The outcome of these meeting should be an updated register, with all the columns up-to-date and a formulated plan agreed upon.
What Should A Risk Register Contain?
The register may contain many different items, and they typically contain the following attributes:
- Risk Name: a brief description of the risk.
- Risk Category: In order to group similar tasks, each one should be categorized in order to allow grouping of similar tasks (e.g. GUI, SW, HW, Testing, etc.)
- Risk Impact: What are the consequences to the project if the risk materializes (happens). An impact is usually a whole number (integer) between 1 and 5. 1 being of low impact, and 5 very high impacts on the project.
- Risk Probability: What are the chances that the risk will materialize during the course of the project. This can be rated in percentages between 20% and 100% in increments of 20%, or by an integer between 1 and 5. The higher the number, the more likely that the risk will materialize during the course of the project.
- Risk Rating (or Risk Number): This is the result of the multiplication of the risk impact and the risk probability. For example, A risk with an impact of 3 and probability of 4 will have a rating of (3 X 4) = 12.
- Risk Mitigation: How all those involved in the project plan on lowering the impact and probability of the risk. Most mitigation plans cost money, and the register should also present the anticipated costs of mitigating the risk.
- Risk Owner: Who has overall accountability for the risk, and is authorized to take action in order to mitigate it.
- Risk Strategy: This is an optional column of the register. It outlines how the project intends in dealing with the risk. The typical attributes are: Avoid, Accept, Control or Transfer.
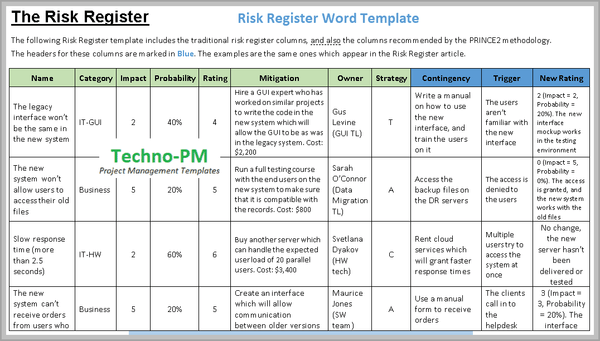
Risk Register Word Template
What Are The Advantages of An Excel Register?
- A central repository which can be accessed by anyone.
- A mechanism by which a project manager can highlight the possible issues in a project.
- Documenting the risks enforces a standard which makes sure all the information is captured.
- Clear accountability of who owns the risks and details about possible mitigation with dates.
- Allows a project manager to maintain an audit log of risks opened and closed.
- Excel Template is commonly used in business so need of a additional software.
- Risk Register gives everyone a clear view of the state of the project.
- Having an excel risk register will also enforce a periodic review of the risks.
When To Report The Poject Risks? The Frequency of Reporting:
- A meeting should be held once every two weeks, and be chaired by the PM or the RMO of the project.
- The RMO will summarize the meetings, track the risks in between and raise red flags to the management team if required (for example: if a risks’ rating has increased).
- In each meeting, the risks should be updated (likelihood, impact, rating, cost, and mitigation) by the risk owner or their proxy.
- The goal is to mitigate each risk until it’s down to acceptable ratings (15 or below).
- Decisions regarding each risk will be made by the meetings’ chair, and these will be captured in the mitigation cell of the register below.
Prince2 Recommendation For The Risk Register:
Projects in a Controlled Environment (PRINCE2) is a project management methodology which was initially conceived by the UK government for use in its IT projects. The method is a framework which can suit any IT project and is principles driven. The method also states that it is possible to organize the risk ratings in a scatter plot chart, for visual visibility of the risk severity.
The methodology recommends the following points for use in a risk register (the first six are similar to the points listed above):
- Categorize risks in order to group similar ones.
- Give each risk a name and brief description.
- Give each risk an impact assessment integer. This may be substituted with a quality attribute (low, medium, high, highest).
- Give each risk a probability that it will materialize (also an integer). This may also be substituted with a quality attribute (low, medium, high, highest).
- Give each risk a score (which is the multiplication of the impact and probability).
- Give each risk a mitigation plan. These steps are typical: Analyze the problem, Plan a Response to the risk, Monitor and Control the risk until it is down to acceptable levels (or has materialized).
- Give each risk a Contingency plan: Which action should be taken to materialize the risk.
- Give each risk a Trigger: An event which will result in the risk materializing (e.g. the server will crash).
- Give each risk a rating post mitigation: Once the mitigation plan has been executed, what is the new score of each risk.
Examples of Risks in IT and Business Projects
| Risk | Mitigation |
|---|---|
| The legacy interface won’t be the same in the new system | Hire a GUI expert who has worked on similar projects to write the code in the new system which will allow the GUI to be as was in the legacy system. Cost: $2,200 |
| The new system won’t allow users to access their old files | Run a full testing course with the end users on the new system to make sure that it is compatible with the records. Cost: $800 |
| Slow response time (more than 2.5 seconds) | Buy another server which can handle the expected user load of 20 parallel users. Cost: $3,400 |
| The new system can’t receive orders from users who have a 2010 version | Create an interface which will allow communication between older versions and ours. Cost: $1,090 |
| The quarterly reports aren’t in the required format (regulation dictated) | Customize the format in the new system. Cost: $250 |
| The new system can’t support more than 25 simultaneous users | None, The peak hours expect no more than 12 simultaneous users. Cost: $0 |



